Okay, so now that we have completed the installation of Exchange 2013 in our environment, it looks like we have a couple more steps before we can actually get email flowing and our users logging in to check their email.
ValidationSteps
1. Verify that your installation completed successfully
Before you start configuring the features of Exchange 2013, it’s best to make
sure that the installation completed successfully. In order to do so, it’s
recommended to perform the following steps:
2. Restart the Server
A server reboot is required for your Exchange Server to properly register and
startup all of it’s required services and dependencies. Some organizations
configure policies explicitly preventing automatic reboots of servers. Please
make sure that your server has rebooted after the installation.
3. Verify the
correct build/version of Exchange is installed
From PowerShell, run the command: Get-ExchangeServer |
Format-List.
The output returned will indicate the version number of Exchange installed on
the server as well as any installed patches. For more information of this
command, click here. For the Preview release
version of Exchange 2013, the build number is 15.0,516,32. Here’s a great link that shows
all of the Build numbers for the different versions of Exchange Server.
4. Check logs for errors
View the application logs on the server under Event Viewer as well as the
ExchangeSetup.log file in the C:ExchangeSetupLogs folder of the Exchange Server
using any text editor. You can perform a search to match the strings “Error” or
“Failed”. This will help you to identify any potential errors. Be sure to visit
the Microsoft Technet Exchange 2013 forums here to seek help from the awesome
online community. (‘I have done so many a time’, says Road Chimp)
The Exchange Administration Center
In Exchange 2013, you have the option of configuring Exchange 2013 via a GUI using the Exchange Administration Center (EAC) or via the Exchange Management Shell. The EAC is a new web-based management interface that is a vastly improved version of the Exchange Control Panel that debuted in Exchange 2010.
To get started with the EAC, you can first find out the URL of your EAC by typing the following command in PowerShell:
Get-EcpVirtualDirectory | fl *URL*
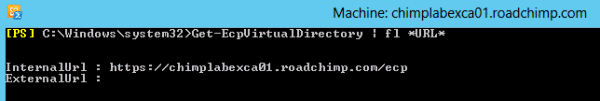
The EAC URL should look something like https://casserver01.corpxyz.com/ECP. Note that the URL ends in ‘ECP’ which is probably a throwback to the ECP in Exchange 2010. You can launch the EAC from a browser. Don’t forget to login via a domain user account and password.
Configuration Steps
So now we’re ready to begin configuring our Exchange 2013 Server. In this section we will configure the following:
1. Create a Send Connector
2. Configure Receive Connector
3. Add additional accepted domains
4. Configure the default email address policy
5. Configure an SSL certificate
6. Configure External URLs
7. Configure DNS
Now, on to our first configuration task:
1. Create a Send Connector
A Send Connector allows you to provide Exchange with instructions on how to send emails outside of your organization. For example, you can define that emails intended for a specific recipient domain can get routed to a specific endpoint server, or simply you can configure the Send Connector to use DNS to make routing decisions for you. To configure a Send Connector via the following steps:
Click on Mail flow > Send connectors.
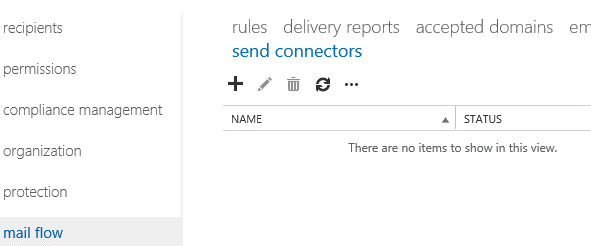
On
the Send connectors page, click Add, which launches the New Send
Connector wizard.
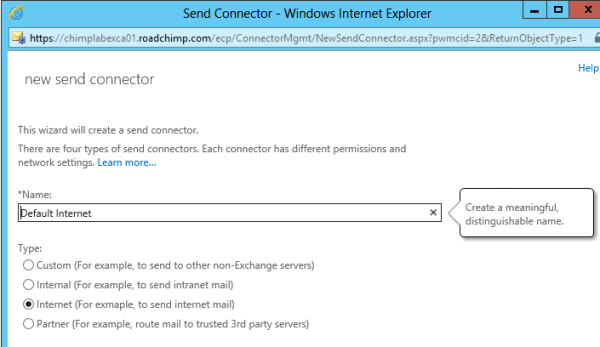
I specified the name “Default Internet” for the send connector. You have four options to select and each selection determines the default permission sets that are assigned on the connector and grants those permissions to trusted security principals (users, computers, security groups etc.).
The options are:
- Custom: Typically when you want to when you want route messages to computers not running Microsoft Exchange Server 2013. You can choose to route mail through smart hosts running SMTP. Microsoft recommends that if you use basic authentication, you use an encrypted connection because the username and password are sent in clear text.
- Internal: Allows you to send intranet mail
- Internet: Allows you to send internet mail
- Partner: Routes mail to allow connections only to 3rd party servers that authenticate with TLS certificates.
For our lab demo, I selected Internet and then clicked Next.
In the next screen,
ensure that “MX record associated with recipient domain” is select and click
Next.
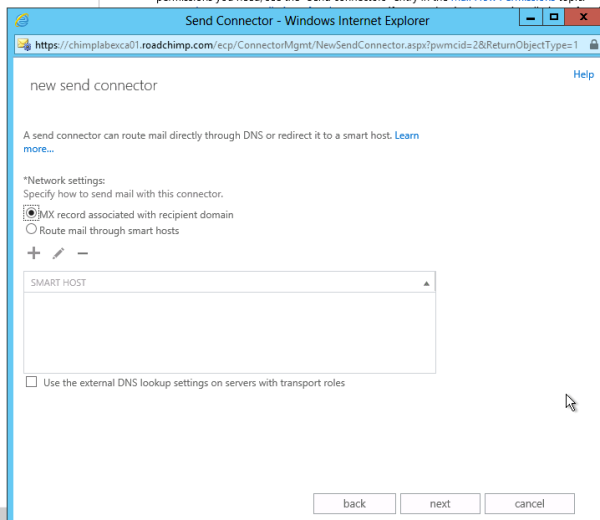
This indicates that the connector uses DNS to route mail. Your other option is to route mail through a smart host*, which could be a dedicated SMTP server or cloud-hosted service that your organization uses to send all out-bound email (and perhaps perform malware and virus scanning).
* The “Use the external DNS lookup settings on servers with transport roles” may be used if you have both external and internal DNS zone files for a domain you need to route mail to and you want emails to be routed via the internet. I left this option unchecked.
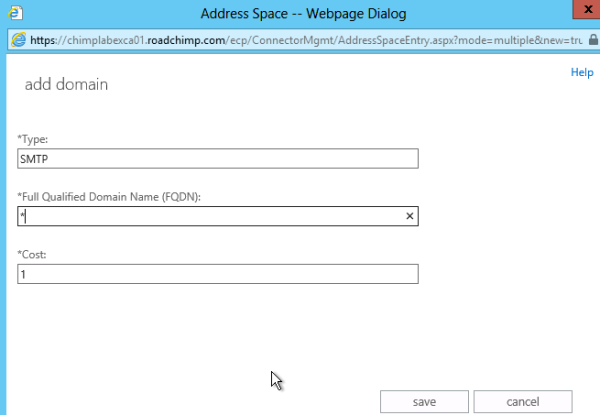
Under Address space,
click Add+. Select SMTP in the Type field and enter * in the Fully Qualified
Domain Name (FQDN) field, with a cost of 1. Click Save.
Note: The Scoped send connector checkbox indicates that this connector is scoped to a specific group of servers (a delivery group) and only this group is allowed to route messages to destination defined by the connector. This delivery group may contain Exchange 2010 Hub Transport servers or Exchange 2013 Mailbox servers located in different Active Directory sites. Ensure that the checkbox isn’t selected and then click Next.
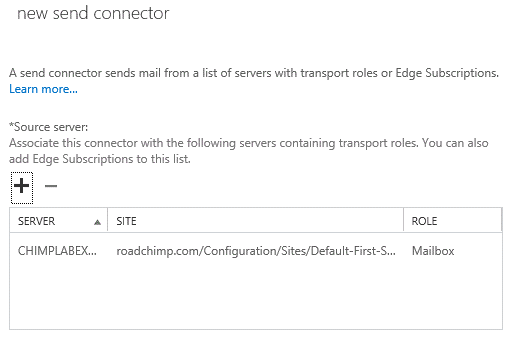
Under Source server, click Add. In the Select a server window, select a Mailbox server that will be used to send mail to the Internet via the Client Access server. I’ve selected my mailbox server CHIMPLABEXMB01. After you’ve selected the server, click Add and then click OK. Now you can click Finish to complete the wizard.
– Optional: Configure the Mailbox Server to proxy outbound messages through a Client Access Server . We can perform this task through the shell by typing in the command:
Set-SendConnector “Default Internet ” –FrontendProxyEnabled
$true
By setting this command, you’re effectively configuring the behavior of the Transport service on the Mailbox servers to route outbound mail through the Front End Transport service on the CAS servers in the local Active Directory site. This is NOT set by default and is a good practice to consolidate and simplify mail flow, especially in large environments.
Simply typing Set-SendConnector provides more information on how to set parameters on a Send connector. It’s useful to note that the default maximum message size, specified by the MaxMessageSize parameter, has been increased from 10MB to 25MB. Another parameter TlsCertificateName has been added. It is used to authenticate the local certificate to be used for outbound connections and minimize the risk of fraudulent certificates.
*Note on SMTP Relays
In the old days, many organizations used to expose their Exchange servers
directly to the Internet. Nowadays, you would have either an SMTP mail
appliance (Anti-Spam/ Malware) or Cloud subscription service that relays
inbound emails to your CAS server. As there is no Edge Server support in
Exchange 2013, you might want to hold on to your Exchange 2010 Edge Servers for
now! Also, you will need to ensure that inbound SMTP is configured on your
firewall to enable your SMTP edge devices to relay emails into your CAS
servers.
– You can verify that this works by logging in to Outlook Web App (https://casserver01.corpxyz.com/OWA) with a valid user account and sending an email to an external recipient.
2. Configure Receive Connector
A receive connector listens for inbound connections that match the settings of a receive connector through a particular IP address and port and from a specified address range. You can configure multiple receive connectors to control which servers receive messages from a particular IP address or IP address range. A receive connector can be created on a Mailbox Server running the Transport service or a Client Access Server running the Front End Transport service.
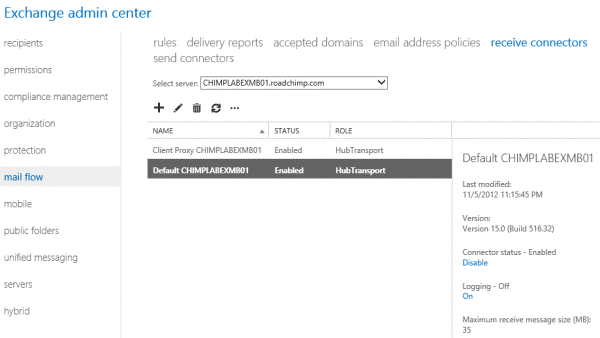
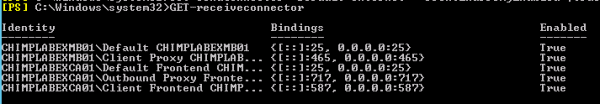
Two receive
connectors are configured automatically after you install a Mailbox Server
running the Transport Service in Exchange 2013. They are:
- Default<server name> Accepts connections from Mailbox servers running the Transport service and from Edge servers.
- Client Proxy <server name> Accepts connections from front-end servers. Typically, messages are sent to a front-end server over SMTP.
Three receive connectors are configured automatically after you install a Client Access Server running the Frontend Transport Service in Exchange 2013. They are:
- Default FrontEnd <server name> Accepts connections from SMTP senders over port 25. This is the common messaging entry point into your organization.
- Outbound Proxy Frontend <server name> Accepts messages from a Send Connector on a back-end server, with front-end proxy enabled.
- Client Frontend <server name> Accepts secure connections, with Transport Layer Security (TLS) applied.
Each connector is assigned a TransportRole value. You can use it to determine the role the connector is running in. This can be helpful in cases where you are running multiple roles on a single server. In the case of each Receive connector running on a Mailbox Server, their TransportRole value is HubTransport. For each Receive connector running on a Client Access Server, their TransportRole value is FrontEndTransport. You can view this information by typing the Get-ReceiveConnector command.
3. Add additional accepted domains
By default, Exchange uses the domain name of the Active Directory Domain where the setup /PrepareAD command was run prior to installing Exchange. Your Organization may want to use a different email address to send and receive emails from. Perform the following steps to configure an accepted domain:
From EAC, click on Mail flow > Accepted domains. On the Accepted domains page, click Add. Specify a name for the accepted domain in the New accepted domain wizard. Now specify the SMTP recipient domain you want to add in the Accepted domain field. If this Exchange Server will be receiving all emails for the domain that you just added, select Authoritative domain and then click Save.
4. Configure the default email address policy
A couple of posts back, we explored the setup PrepareSchema command and how it extends the schema to provide support for mail-enabled objects in Active Directory. The default email address policy enables you to setup rules to assign every recipient in your organization with a default email address based on the accepted domain that you configured previously. For example: JSmith@contoso.com.
If you added an accepted domain in the previous step and you want that domain to be added to every recipient in the organization, you need to update the default email address policy. Perform the following steps in the EAC:
Go to Mail flow > Email address policies. On the Email address policies page, select Default Policy and then click Edit.
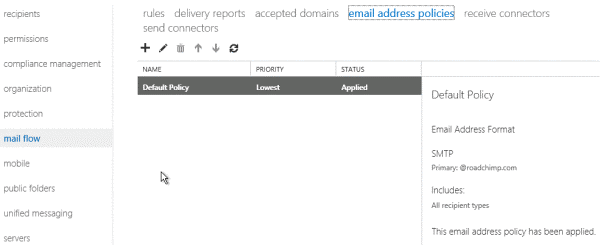
Click Email Address Format on the Default Policy Email Address Policy page. Click the SMTP address you want to change and then click EditUnder Email address format. Specify the SMTP recipient domain you want to apply to all recipients in the Exchange organization.
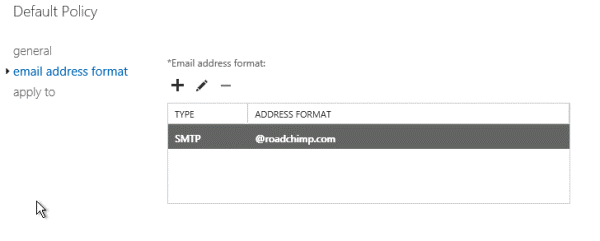
On the Email address format page in the Email address
parameters field. (This domain must match the accepted domain you added in
the previous step.) Click Save.
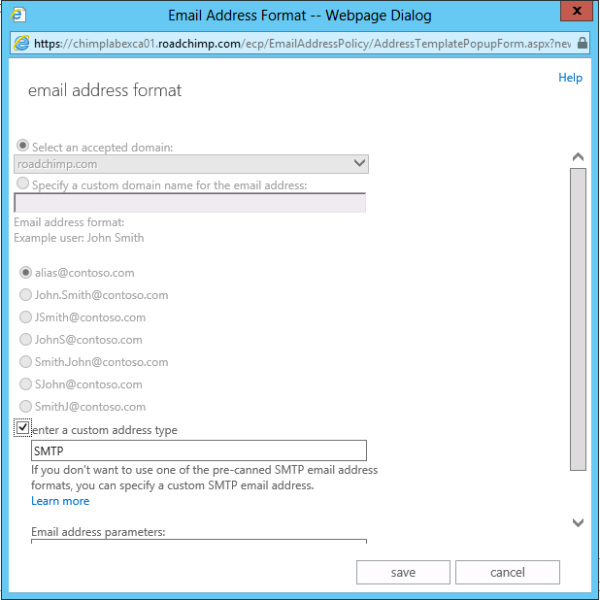
Click Save again and then click Apply in the Default Policy details pane.
You can verify that this works by selecting a mailbox in EAC (Recipients>Mailboxes) and verifying that the User Mailbox field has been set to alias@corpxyz.com. Alternatively, you can try creating a mailbox in EAC (Recipients>Mailboxes and Add+). You can now provide all the information required to create a new mailbox.
5. Configure an SSL certificate
Services such as Outlook Anywhere and ActiveSync require certificates to be configured on your Exchange 2013 server. The following steps show you how to configure an SSL certificate from a third-party certificate authority (CA):
– Go
to Servers > Certificates. On
the Certificates page, select the Client Access server in the Select
server field, and then click Add
– This launches the New Exchange certificate wizard. Now select Create
a request for a certificate from a certification authority and then
click Next.
– Specify a name for this certificate then click Next.
– You can request a wildcard certificate by selecting Request
a wild-card certificate and then specifying the root domain of all subdomains in
the Root domain field. Alternatively, leave this page blank and
click Next.
– Click Browse and specify an Exchange server to store the
certificate on. You must select an Internet-facing Client Access server.
Click Next.
– For each service in the list shown, specify the external or internal
server names that users will use to connect to the Exchange server. For
example, for Outlook Web App (when accessing over the Internet), you might
specify webmail.roadchimp.com. For OWA (when
accessing over the Intranet), you might specify CAS01.roadchimp.com. These domains will
be used to create the SSL certificate request. Click Next.
– Add any additional domains you want included on the SSL certificate.
Click Next.
– Provide information about your organization. This information will be
included with the SSL certificate. Click Next.
– Specify the network location where you want this certificate request to
be saved. Click Finish.
After you’ve saved the certificate request, submit the request to your certificate authority (CA). This can be an internal CA or a third-party CA, depending on your organization. Clients that connect to the Client Access server must trust the CA that you use. After you receive the certificate from the CA, complete the following steps:
– On
the Server > Certificates page in the EAC, select the
certificate request you created in the previous steps.
– In the certificate request details pane,
click Complete under Status.
– On the complete pending request page, specify the path to the SSL certificate
file and then click OK.
– Select the new certificate you just added, and then click Edit.
– On the certificate page, click Services.
– Select the services you want to assign to this certificate. At minimum,
you should select SMTP and IIS. Click Save.
– If you receive the warning Overwrite the existing default SMTP
certificate?, click OK.
To verify that you
have successfully added a new certificate, do the following:
– In the EAC, go to Servers > Certificates.
– Select the new certificate and then, in the certificate details pane,
verify that the following are true:
Status shows Valid
Assigned to services shows IIS and SMTP
6. Configure External URLs
Now that you’ve published the external domain names in a certificate and installed them into Exchange, you need to configure the external domains on the Client Access server’s virtual directories and then configure your domain name service (DNS) records.
The steps below configure the same external domain on the external URL of each virtual directory. To configure different external domains on one or more virtual directory external URLs, you will have to configure the external URLs manually. For more information, see Virtual Directory Management.
– Go to Servers > Servers and
then click on the Wrench > Configure external access domain.
– Under Select the Client Access servers to use with the external URL,
click Add
– Select the Client Access servers you want to configure and then
click Add. After you’ve added all of the Client Access servers you want to
configure, click OK.
– In Enter the domain name you will use with your external Client Access
servers, type the external domain you want to apply, for example: mail.roadchimp.com. Click Save.
– Go to Servers > Servers, select the name of the
Internet-facing Client Access server (CHIMPLABEXCA01 in my case) and
then click Edit.
– Click Outlook Anywhere.
In the Specify the external hostname field, specify the externally
accessible FQDN of the Client Access server. For example, mail.roadchimp.com. You can also verify
the internal FQDN that users will access the host from .Click Save.
7. Configure DNS
After you’ve configured the external URL on the Client Access server virtual directories, you need to configure DNS records for Autodiscover, Outlook Web App, and mail flow. The DNS records should point to the external IP address of your Internet-facing Client Access server and use the externally accessible FQDNs that you’ve configured on your Client Access server. The following are examples of recommended DNS records that you should create to enable mail flow and external client connectivity.
| FQDN | DNS record type | Value |
| roadchimp.com | MX | Mail.roadchimp.com |
| Mail.roadchimp.com | A | <external ip> |
| Owa.roadchimp.com | A | <external ip> |
| Autodiscover.roadchimp.com | A | <external ip> |
To verify that you have successfully configured the external URL on the Client Access server virtual directories, do the following:
– In the EAC, go
to Servers > Virtual directories.
– In the Select server field, select the Internet-facing Client
Access server.
– Select a virtual directory and then, in the virtual directory details
pane, verify that the External URL field is populated with the
correct FQDN and service as shown below:
| Virtual directory | External URL value |
| Autodiscover | No external URL displayed |
| ECP | https://mail.roadchimp.com/ecp |
| EWS | https://mail.roadchimp.com/EWS/Exchange.asmx |
| Microsoft-Server-ActiveSync | https://mail.roadchimp.com/Microsoft-Server-ActiveSync |
| OAB | https://mail.roadchimp.com/OAB |
| OWA | https://mail.roadchimp.com/owa |
| PowerShell | http://mail.roadchimp.com/PowerShell |
To verify that you have successfully configured DNS, do the following:
– Open a command
prompt and run nslookup.exe.
– In nslookup, look up the A record
of each FQDN you created. Verify that the IP address that’s returned for each
FQDN is correct.
– In nslookup, type set type=mx and then look up the accepted domain you
added in Step
– Verify that the value returned matches the FQDN of the Client Access server.
Summary:
So in this post, we’ve gotten past all the configuration steps to get Exchange 2013 up and running. We’ve configured Send and Receive connectors, as well as accepted email address policies. We configured a SSL Certificate to support client access via ActiveSync and OutlookAnywhere. Finally, we configured external DNS settings to enable Exchange to receive emails from the rest of the world.
In the next post, we will peer behind the hood of Exchange 2013 and learn a bit more abou the Mail Routing and Mail Flow behavior of Exchange as well as Exchange’s new Storage Engine.
Road Chimp, signing out.
